As a seasoned tech enthusiast, I’ve always been fascinated by the ever-evolving landscape of cybersecurity. Quantum computing, with its promise of exponential processing power, is poised to revolutionize many industries, including blockchain technology.
In this article, we delve into the intriguing intersection of quantum computing and blockchain security. The advent of quantum computing brings both excitement and concern to the world of cybersecurity. While quantum computers hold the potential to crack traditional encryption methods, they also offer new possibilities for enhancing blockchain security protocols.
Join me as we explore the implications of this technological advancement on the integrity and resilience of blockchain networks. In the realm of cybersecurity, staying ahead of the curve is paramount.
With quantum computing on the horizon, understanding its impact on blockchain security is not just a matter of curiosity but a necessity for safeguarding digital assets in the future.
Understanding Quantum Computing Basics
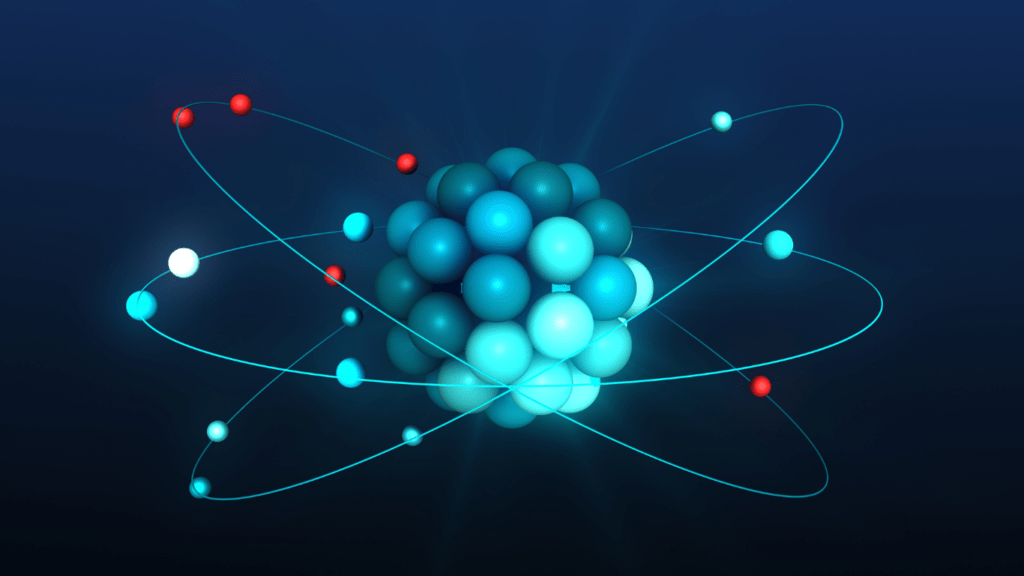
Quantum computing operates on principles of quantum mechanics, utilizing quantum bits or qubits as basic units of data. These qubits can exist in multiple states simultaneously, unlike classical binary bits.
The concept of superposition allows qubits to represent both 0 and 1 at the same time, enabling quantum computers to perform complex calculations much faster than classical computers. In addition to superposition, quantum computers leverage the unique property of entanglement.
Entangled qubits are interconnected in a way that the state of one qubit directly influences the state of another, regardless of the physical distance between them. This phenomenon enables quantum computers to process vast amounts of information in parallel, exponentially increasing their computational power.
Another fundamental aspect of quantum computing is quantum tunneling. Quantum tunneling allows qubits to traverse energy barriers that classical bits cannot overcome, enabling quantum computers to solve complex problems more efficiently.
By harnessing these distinctive characteristics of qubits, quantum computing has the potential to revolutionize various industries, including cybersecurity and blockchain technology.
How Quantum Computing Threatens Blockchain Security
Quantum Computing’s Threat to Cryptographic Algorithms
I’ll now delve into the specific risks posed by quantum computing to cryptographic algorithms used in blockchain security. Quantum computers have the potential to break traditional cryptographic schemes, including the widely used RSA encryption and Elliptic Curve Cryptography (ECC).
These algorithms, which secure digital transactions on blockchain networks, rely on mathematical problems that are difficult for classical computers to solve efficiently. However, quantum computers can leverage their immense processing power to factor large numbers quickly, compromising the security of these encryption methods.
Risks of Quantum Attacks on Blockchain Networks
In the context of blockchain networks, quantum attacks could undermine the integrity and confidentiality of transactions. The immutability of blockchain, which is maintained through cryptographic hashing, could be compromised if quantum computers can reverse these hash functions efficiently.
This could allow malicious actors to alter transaction records, leading to fraudulent activities and the erosion of trust in decentralized systems. Moreover, the transparent nature of blockchain, which ensures data integrity through consensus mechanisms, may also be vulnerable to quantum attacks, posing a significant threat to the security of digital assets stored on the blockchain.
Current Solutions and Future Strategies
Exploring current solutions and future strategies in the realm of quantum computing and blockchain security is crucial to staying ahead of potential threats posed by quantum advancements.
- Post-Quantum Cryptography: Leveraging post-quantum cryptographic algorithms is a proactive approach to fortifying blockchain security against quantum attacks. As quantum computers evolve, traditional encryption methods could become obsolete, making the adoption of quantum-resistant algorithms essential.
- Quantum Key Distribution (QKD): Implementing QKD protocols enhances the security of cryptographic key exchanges in blockchain networks. QKD leverages the principles of quantum mechanics to secure communication channels, offering a quantum-safe solution for protecting sensitive data transmissions.
- Blockchain Consensus Mechanisms: Enhancing blockchain consensus mechanisms with quantum-resistant algorithms can bolster the network’s resilience to quantum threats. By integrating post-quantum consensus protocols, blockchain platforms can mitigate the risks posed by quantum attacks on transaction validation and network integrity.
- Continuous Research and Development: Investing in ongoing research and development efforts is essential for adapting blockchain security measures to address evolving quantum computing capabilities.
- Education and Awareness: Promoting awareness and understanding of quantum computing’s impact on blockchain security is critical for fostering a proactive cybersecurity culture. Educating stakeholders about quantum risks and mitigation strategies empowers them to make informed decisions in safeguarding digital assets on blockchain platforms.
- Multi-Layered Security Approaches: Implementing multi-layered security approaches that combine traditional encryption techniques with quantum-safe measures can enhance the overall resilience of blockchain systems. By diversifying security layers, organizations can create robust defense mechanisms to mitigate quantum threats effectively.
As quantum computing continues to advance, adopting a proactive stance towards strengthening blockchain security is paramount in safeguarding digital assets against emerging quantum risks. By implementing current solutions and embracing future strategies tailored to the quantum landscape, organizations can fortify their blockchain ecosystems and uphold the integrity of decentralized transactions.
Implications for the Future of Blockchain Security
Exploring the future implications of quantum computing on blockchain security reveals significant challenges and the need for proactive measures to safeguard digital assets. Quantum computing’s rapid advancements pose a potential threat to traditional encryption methods and blockchain security protocols, necessitating a strategic approach to enhance resilience in the face of evolving technology.
The integration of quantum computing in cybersecurity raises concerns about the vulnerability of current cryptographic algorithms used to secure blockchain transactions. Traditional schemes like RSA encryption and Elliptic Curve Cryptography (ECC) may face compromise under the computational power of quantum computers, which excel at factoring large numbers efficiently. This capability could jeopardize the confidentiality and integrity of blockchain transactions, introducing the risk of malicious actors tampering with transaction records and undermining trust in decentralized systems.
To counter these quantum threats, the future of blockchain security lies in embracing post-quantum cryptographic algorithms to fortify defenses against potential attacks. The adoption of Quantum Key Distribution (QKD) protocols for secure key exchanges and the integration of quantum-resistant algorithms into blockchain consensus mechanisms are crucial steps to enhance network security. Ongoing research and development efforts are vital to stay ahead of quantum capabilities, with a focus on educating stakeholders about the risks posed by quantum computing.
Moving forward, a multi-layered security approach that combines traditional security measures with quantum-safe protocols will be essential to mitigate emerging threats effectively. By taking a proactive stance and adapting security measures to match the pace of quantum advancements, the blockchain ecosystem can uphold the integrity of digital assets and ensure continued trust in decentralized systems amidst evolving technological landscapes.


























































































































































































































































































































































































































































































































































































































































 Joselito Huntterly has made significant contributions to Lend Crypto Volt by enhancing its technical foundations. With a background in software development and cybersecurity, Joselito has implemented robust systems to ensure the platform's security and reliability. His expertise in emerging technologies has also helped streamline content delivery, ensuring users receive timely updates and insights. Joselito's dedication to creating a secure and efficient platform is essential for users navigating the dynamic world of cryptocurrency.
Joselito Huntterly has made significant contributions to Lend Crypto Volt by enhancing its technical foundations. With a background in software development and cybersecurity, Joselito has implemented robust systems to ensure the platform's security and reliability. His expertise in emerging technologies has also helped streamline content delivery, ensuring users receive timely updates and insights. Joselito's dedication to creating a secure and efficient platform is essential for users navigating the dynamic world of cryptocurrency.